Good Password Checker
Reposting this on the new system because it’s a great password checker.
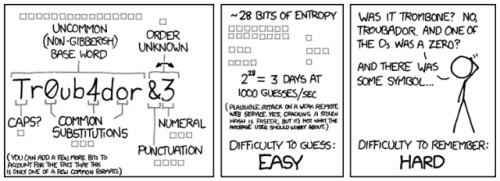
One of my favourite Web comics, xkcd, illustrates the biggest problems I have with passwords in general, and specifically Web-based passwords, namely that they are easy to hack and difficult to remember. Worst of all are those forms which require a fixed number of characters … like exactly 7 characters. Unbelievable.
Not as bad, but which still bug me beyond belief, are those which require capital/lowercase letter combinations, a number, and a special character. Most of us, looking at that set of requirements are almost always going to immediately think of putting a “#1” on the end of what we’d already planned to use.
What we really want, and what we need desperately, is something that’s easy to remember, but difficult to guess, and difficult to brute-force. That means adding entropy. That means a longer password is better. Especially if someone’s looking over your shoulder.
Most password strength checkers look only for the attributes mentioned in the above comic, and do nothing for our security. We invariably use passwords that we soon forget, or that a computer can easily hack.
Sure, increasing the pool of characters (by requiring special characters, spaces, numbers, and mixed-case letters) will help to challenge any computer attack, but so will increasing the length of the overall password … or passphrase.
And a passphrase is easier for you to remember, so you don’t have to entrust your password to a Post-It note, or a password keeper, itself guarded by an easy password.
You know it’s bad when 4 random words put together form a better password than all the ones you’ve previously been using, or that you are forced to use on a website.
Vista-password (Photo credit: Wikipedia)
I found a really good password checker that integrates entropy as part of its check. It comes from http://rumkin.com
People wonder if their password is a good password. I often come across two distinct groups of people. The first would fall into a “just use any word” category, which is a very bad practice for picking passwords. The second group will mix in a few numbers in order to make the password a lot harder to guess. But, how do you know if you have a secure passphrase?
Good passwords / passphrases:
… should be 8 characters or longer, which forces you to use multiple words or extra symbols.
… should have upper case, lower case, symbols, and numbers; or at least three of those four groups.
… should not be a common word and should not be a common phrase.
… should not contain a date, a name, or other things that can be associated with you.
… should be created randomly or semi-randomly.This password checker will gauge your password and give it a score based on how good of a password it is. It will let you know if you picked a common password (don’t do that!) and it will also take into account the probability of letters landing close to each other. For instance, “Q” is almost always followed by “U”, so your password’s score won’t increase much when you type in the “U”.
I use cryptographically-minded descriptions to describe how weak or strong a password is. For email accounts, passwords to log into your personal machine, and other things that don’t require the most strict authentication, feel free to use a password that is deemed “Weak” or “Reasonable”.
This runs completely in your browser and sends no information to anyone. If you are paranoid, you can read the source code, unplug your machine from the internet, or just use a password that is similar to yours. Also, please keep in mind that this is an estimate of how strong your password is, and there is no guarantee that the information shown is correct.
- Warnings are shown if you enter a common password.
- Warnings are shown if your password is very short (4 or less characters) or if it is short (less than 8 characters)
Password strength is determined with this chart, which might be a bit of a stretch for a non-critical password:
< 28 bits = Very Weak; might keep out family members 28 – 35 bits = Weak; should keep out most people, often good for desktop login passwords 36 – 59 bits = Reasonable; fairly secure passwords for network and company passwords 60 – 127 bits = Strong; can be good for guarding financial information 128+ bits = Very Strong; often overkill The number of bits listed for entropy is an estimate based on letter pair combinations in the English language. To make the frequency tables a reasonable size, I have lumped all non-alphabetic characters together into the same group. Because of this, your entropy score will be lower than your real score when you use several symbols.
For determining the character set, letters are grouped into a-z, A-Z, numbers, symbols above numbers, other symbols, and other characters. If your passphrase contains a character from the subset, that subset is added to the pool, increasing the size of the character set and increasing the amount of entropy in your password.For further information, try NIST’s Special Publication 800-63, Electronic Authentication Guideline, Appendix A: Estimating Password Entropy and Strength. Also, C.E. Shannon‘s A Mathematical Theory of Communication.